| CPC H04L 63/1416 (2013.01) [H04L 63/0236 (2013.01); H04L 63/123 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01)] | 20 Claims |
|
1. A system comprising:
a first computing device communicatively coupled to a network; and
a second computing device comprising:
a processor; and
non-transitory memory storing instructions that, when executed by the processor, causes the second computing device to:
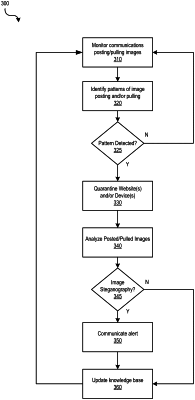
identify a pattern of file transfers comprising pushing and retrieving a same file multiple times between the first computing device on a secure network and a common group of image hosting websites, wherein the pattern is identified via simulations of a simulated command and control server environment;
quarantine, based on an identification of the pattern of file transfers associated with the first computing device, the first computing device from the secure network;
identify, in at least one file transferred between the first computing device and the simulated command and control server environment, an indication of steganography; and
trigger, based on an identified indication of steganography, an alert identifying that the first computing device had been compromised by command and control malware.
|