| CPC H04L 63/0853 (2013.01) [G06F 21/335 (2013.01); G06F 21/602 (2013.01); G06F 21/6209 (2013.01); G06F 21/72 (2013.01); G06F 21/73 (2013.01); H04L 63/0428 (2013.01); H04L 63/062 (2013.01); H04L 67/60 (2022.05); H04W 12/0431 (2021.01); H04W 12/06 (2013.01); H04W 12/35 (2021.01); G06F 2221/2107 (2013.01); G06F 2221/2135 (2013.01); G06F 2221/2145 (2013.01); G06F 2221/2149 (2013.01); G06F 2221/2153 (2013.01); H04L 63/123 (2013.01)] | 20 Claims |
|
1. A target device comprising:
a System on Chip (SoC);
a register interface located on a SoC bus; and
a cryptographic circuit to control feature activation, configuration management, and secure key management of the target device, wherein the cryptographic circuit is accessed via the register interface, wherein the cryptographic circuit is to:
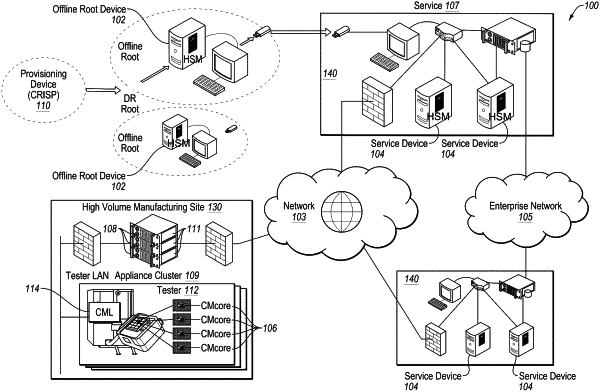
receive a module sequence from a tester device located at a first facility during an operation phase of a manufacturing lifecycle of the target device, wherein the tester device is operatively coupled to the target device and is an untrusted device, wherein the module sequence is generated by a module, the module being an application that, when executed by an appliance device, securely provisions a data asset to the target device via the tester device; and
perform a sequence of operations that securely provisions the data asset of the module to the SoC.
|