| CPC H04L 63/0471 (2013.01) [G06F 3/062 (2013.01); G06F 3/067 (2013.01); G06F 3/0655 (2013.01); G06F 21/602 (2013.01); G06F 21/62 (2013.01); G06F 21/645 (2013.01); G06Q 20/383 (2013.01); G06Q 20/3829 (2013.01); G06Q 20/38215 (2013.01); G06Q 20/401 (2013.01); H04L 9/0643 (2013.01); H04L 9/083 (2013.01); H04L 9/0819 (2013.01); H04L 9/0825 (2013.01); H04L 9/0833 (2013.01); H04L 9/0891 (2013.01); H04L 9/14 (2013.01); H04L 9/30 (2013.01); H04L 9/3218 (2013.01); H04L 9/3236 (2013.01); H04L 9/3242 (2013.01); H04L 9/3247 (2013.01); H04L 9/3263 (2013.01); H04L 9/3265 (2013.01); H04L 9/3268 (2013.01); H04L 63/0421 (2013.01); H04L 63/0442 (2013.01); H04L 63/083 (2013.01); H04L 63/101 (2013.01); H04L 63/102 (2013.01)] | 29 Claims |
|
1. A method, comprising:
participating, by a particular recipient, in a data storage system, wherein:
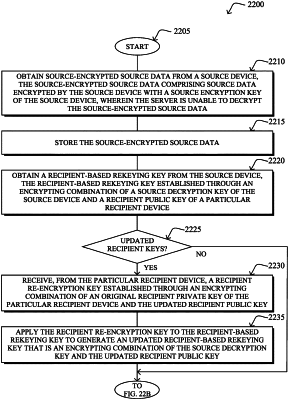
i) a storage server is configured to obtain and store source-encrypted source data received from a source, the source-encrypted source data comprising source data encrypt-ed by the source with a source encryption key of the source, wherein the storage server is unable to decrypt the source-encrypted source data;
ii) the source is configured to establish and send a recipient-based rekeying key to the storage server, the recipient-based rekeying key established through an encrypting combination of a source decryption key of the source and a recipient public key of the particular recipient; and
iii) the storage server is further configured to re-encrypt the source-encrypted source data with the recipient-based rekeying key in response to a request to share the source data with the particular recipient, the re-encrypting resulting in recipient-based encrypted source data that is the source data encrypted with the recipient public key of the particular recipient, wherein the storage server is unable to decrypt the recipient-based encrypted source data;
receiving, at the particular recipient from the storage server, the recipient-based encrypted source data;
decrypting, by the particular recipient, the recipient-based encrypted source data using a recipient private key of the particular recipient to obtain the source data; and
processing, by the particular recipient, the decrypted source data,
wherein an intermediate reporting device is configured to receive a set of transaction-based information, the set of transaction-based information readable by the intermediate reporting device, wherein the intermediate reporting device is configured to:
receive the recipient-based encrypted source data, the recipient-based encrypted source data unreadable by the intermediate reporting device;
read the set of information;
create a report based on the set of information;
package the recipient-based encrypted source data with the report; and
send the packaged report and recipient-based encrypted source data to the particular recipient;
wherein the method further comprises:
receiving the packaged report and recipient-based encrypted source data from the intermediate reporting device; and
processing the report with the source data decrypted from the recipient-based encrypted source data.
|