| CPC H04L 63/029 (2013.01) [H04L 12/4633 (2013.01); H04L 12/4641 (2013.01); H04L 12/66 (2013.01); H04L 45/50 (2013.01); H04L 45/54 (2013.01); H04L 45/72 (2013.01); H04L 45/74 (2013.01); H04L 63/0263 (2013.01); H04L 63/0272 (2013.01); H04L 63/08 (2013.01); H04L 63/10 (2013.01); H04W 48/16 (2013.01); H04W 48/18 (2013.01); H04W 76/12 (2018.02); H04W 88/16 (2013.01)] | 14 Claims |
|
1. A method comprising:
receiving, by an access controller and from a networking device, a request for network access, wherein the request indicates a context associated with the networking device, the network access, or a combination thereof;
creating a first networking tunnel with a first gateway to provide a dedicated network route between the networking device and a first network segment accessed via the first gateway;
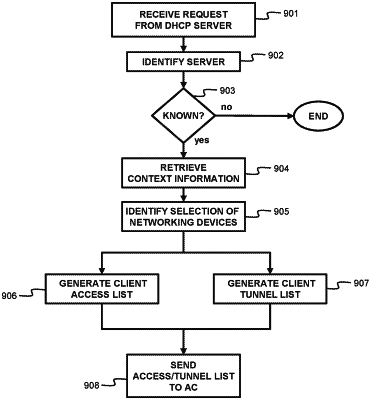
receiving, by an access controller, access rules fora networking device,
wherein the access rules identify a source and destination of packets from the networking device and an application of the networking device;
wherein the access rules are determined for the networking device based on the context;
wherein the access rules comprise firewall rules for the first gateway;
sending, by the access controller, the access rules to the first gateway, wherein the first gateway uses the access rules to apply the firewall rules;
looking up a routing table based on the source of packets from the networking device;
selecting, using the routing table, a virtual network device having an existing networking tunnel dedicated to the destination of packets from the networking device, wherein the existing networking tunnel corresponds to the application of the networking device.
|