| CPC G06Q 20/3678 (2013.01) [H04L 9/083 (2013.01); H04L 9/085 (2013.01); H04L 9/0861 (2013.01); H04L 9/0891 (2013.01); H04L 9/0894 (2013.01); H04L 9/0897 (2013.01); H04L 9/14 (2013.01); H04L 9/3247 (2013.01); H04L 9/50 (2022.05); H04L 2209/56 (2013.01)] | 20 Claims |
|
1. A method comprising:
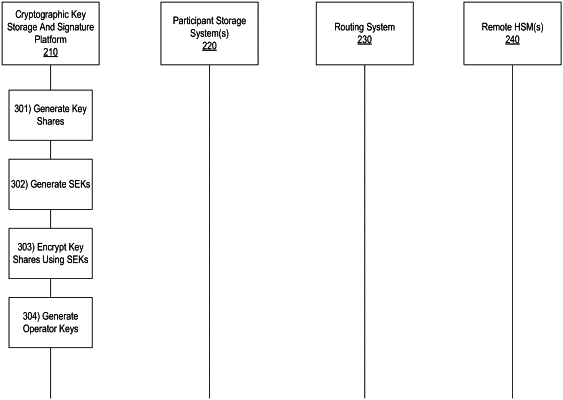
splitting, by a computing platform comprising at least one processor, a communication interface, and memory, a cryptographic signature key into a plurality of cryptographic key shares, wherein the cryptographic signature key may be derived using a quorum number of the plurality of cryptographic key shares;
generating a plurality of encrypted cryptographic key shares and a plurality of share encryption keys (SEKs) by, for each respective cryptographic key share of the plurality of cryptographic key shares:
generating a corresponding SEK for the respective cryptographic key share; and
encrypting, using the corresponding SEK, the respective cryptographic key share to create a corresponding encrypted cryptographic key share;
generating a plurality of encrypted SEKs and a plurality of operator keys by, for each respective SEK of the plurality of SEKs:
generating a corresponding operator key for the respective SEK; and
encrypting, using the corresponding operator key, the respective SEK to create a corresponding encrypted SEK;
distributing the plurality of operator keys corresponding to the plurality of encrypted SEKs to a plurality of end user devices (EUDs) by, for each EUD of the plurality of EUDs:
providing a corresponding operator key to a hardware security module (HSM) of the respective EUD, wherein the HSM is configured to prevent unauthorized copying of the corresponding operator key;
storing, by the computing platform, the plurality of encrypted cryptographic key shares, the plurality of encrypted SEKs, and indications identifying, for each respective encrypted SEK of the plurality of encrypted SEKS, the respective EUD storing the corresponding operator key;
receiving, from a first subset of EUDs, requests to download an encrypted SEK corresponding to each respective EUD of the first subset of EUDs, wherein the first subset of EUDs comprises at least the quorum number of EUDs;
sending, to each EUD of the first subset, a respective encrypted SEK of the plurality of encrypted SEKs;
receiving, from each EUD of a second subset of EUDs, a corresponding decrypted SEK decrypted by a respective EUD using the operator key stored in an HSM of the respective EUD;
decrypting, using the decrypted SEKs received from the second subset of EUDs and based on determining that the second subset of EUDs comprises at least the quorum number of EUDs, corresponding encrypted cryptographic key shares; and
reconstructing, using a reconstruction algorithm and the quorum number of the plurality of decrypted cryptographic key shares, the cryptographic signature key.
|