| CPC G06F 21/316 (2013.01) [G06N 7/00 (2013.01); G06N 20/00 (2019.01); H04L 63/0861 (2013.01); H04L 63/1425 (2013.01); H04W 12/062 (2021.01); H04W 12/065 (2021.01); H04W 12/068 (2021.01); G06F 2221/2139 (2013.01); H04L 63/102 (2013.01)] | 28 Claims |
|
1. A system comprising:
at least one data processor;
memory storing instructions, which when executed by at least one data processor, result in operations comprising:
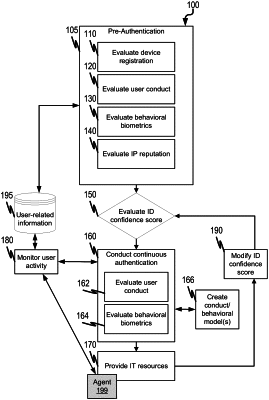
determining an identification confidence score for a user as part of a pre-authentication procedure which includes a device registration evaluation in which a user device is recognized as being associated with the user, the identification confidence score indicating a level of trust that the user is who it purports to be;
initiating authentication for the user based on the identification confidence score of the user being below a predefined level, the authentication comprising:
continuously monitoring, using a trained machine learning model unique to the user, both of user conduct and behavioral biometrics associated with the user in connection with utilization of one or more resources by the user to generate first data;
determining, based on the monitoring, differences between the first data and historical utilization data for the user to determine whether the user's utilization of the one or more resources is anomalous; and
removing, when the user's utilization of the one or more resource is anomalous, the user's access to the one or more resources; and
bypassing the authentication for the user based on the identification confidence score of the user being at or above the predefined level.
|