| CPC G06F 11/008 (2013.01) [G06F 18/2148 (2023.01); G06F 18/24 (2023.01); G06F 21/54 (2013.01); G06F 21/552 (2013.01); G06F 21/577 (2013.01)] | 20 Claims |
|
1. A method for assessing a likelihood of exploitation of software vulnerabilities, comprising:
utilizing a processor in operable communication with at least one memory for storing instructions that are executed by the processor to perform operations, including:
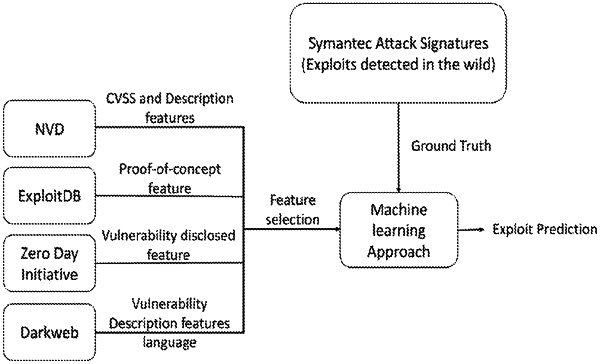
accessing a plurality of datasets associated with a predetermined set of data sources, the plurality of datasets including training data comprising hacker communications;
accessing features from the plurality of datasets that include measures computed from social connections of users posting hacking-related content
applying learning algorithms to the training data to generate classification models that are configured to predict class labels defining a likelihood of exploitation of respective software vulnerabilities;
accessing one or more features associated with a software vulnerability; and
computing, by applying the one or more features to the classification model, a class label defining one or more values defining a likelihood of exploitation associated with the software vulnerability, wherein the likelihood of exploitation predicts an actual exploitation of the respective software vulnerabilities before disclosure based on the hacker communications from the training data.
|