| CPC H04W 12/06 (2013.01) [H04L 9/085 (2013.01); H04L 9/0844 (2013.01); H04L 9/3066 (2013.01); H04L 9/3263 (2013.01); H04L 63/0823 (2013.01); H04L 63/0869 (2013.01); H04L 63/101 (2013.01); H04W 12/04 (2013.01); H04W 12/08 (2013.01); H04W 76/10 (2018.02); H04L 2209/80 (2013.01); H04W 84/12 (2013.01)] | 20 Claims |
|
1. A method, comprising:
establishing, by a first device associated with a network service provider, a network connection with a second device,
wherein the network connection is associated with a wireless connection to the second device;
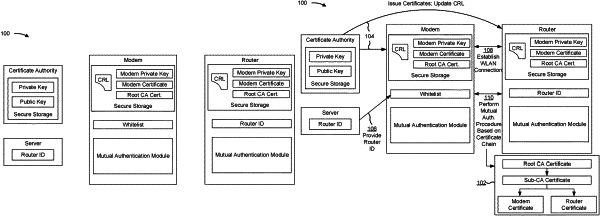
providing, by the first device and based on determining that an authentication certificate is no longer valid, limited connectivity to the second device that limits connectivity of the second device to one or more destinations associated with an identifier in a whitelist,
wherein the one or more destinations correspond to a certificate authority;
performing, by the first device and based on providing the limited connectivity to the second device, an authentication procedure with the second device;
determining a keyset from one or more shared secrets that are calculated based on a private ephemeral key and a public key included in a certificate associated with the second device:
encrypting, based on the keyset, communications via the network connection;
maintaining, by the first device and based on the authentication procedure being successful, the network connection; and
providing, by the first device and based on the authentication procedure being successful, wide area network (WAN) access to the second device.
|