| CPC H04L 9/3247 (2013.01) [G06F 8/65 (2013.01); G06F 21/572 (2013.01); H04L 9/3236 (2013.01); H04L 9/3239 (2013.01)] | 17 Claims |
|
1. An intelligent electronic device (IED) comprising:
at least one sensor coupled to an electrical distribution system, the at least one sensor configured to measure at least one parameter of the electrical distribution system and generate at least one analog signal indicative of the at least one parameter;
at least one analog-to-digital converter configured to receive the at least one analog signal and convert the at least one analog signal to at least one digital signal;
at least one memory configured to store a plurality of firmware packages of the IED;
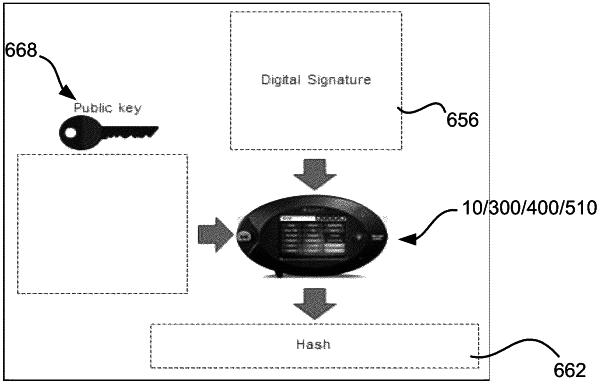
at least one communication interface configured to receive at least one communication, the at least one communication including a digital signature and an unencrypted file, the unencrypted file including firmware data; and
at least one processor configured to receive the at least one digital signal and calculate at least one power parameter of the electrical distribution system, the at least one processor further configured to:
receive the at least one communication from the at least one communication interface,
decrypt the digital signature to obtain a first value,
execute a hash function on the unencrypted file to obtain a second value,
determine if the first value and second value match, and
update at least one firmware package of the plurality of firmware packages stored in the at least one memory with the unencrypted file if it is determined that the first value and the second value match,
wherein the at least one processor is further configured to determine unused sections in the firmware data of the unencrypted file and fill at least one section of the unused sections of the firmware data of the unencrypted file with arbitrary values to impede a third party from determining unused sections of the firmware data before updating the at least one firmware package.
|