| CPC H04L 9/302 (2013.01) [H04L 9/002 (2013.01); H04L 9/0869 (2013.01); H04L 9/0894 (2013.01); H04L 2209/26 (2013.01)] | 20 Claims |
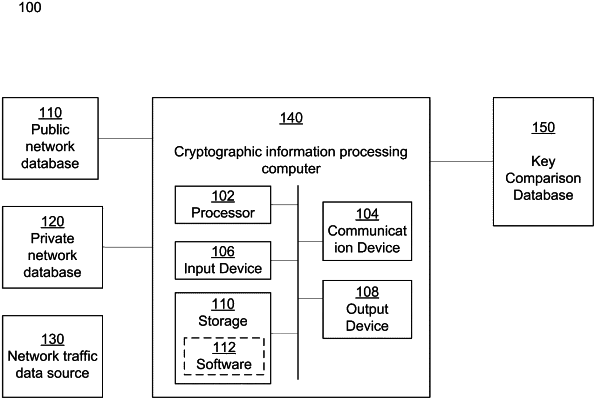
|
1. A system for determining whether a private signing key is vulnerable to being compromised, the system comprising one or more microprocessors configured to cause the system to:
receive cryptographic data comprising a plurality of digital signatures from one or more parties, wherein each of the plurality of digital signatures are based on a respective random number and respective private signing key;
determine that the same random number is used by the same party for more than one digital signature;
in accordance with a determination that the same random number is used by the same party for more than one digital signature, determine that the private signing key of that party is vulnerable to being compromised; and
generate an alert indicating that the private signing key of the respective party is vulnerable to being compromised.
|