| CPC H04L 9/0894 (2013.01) [G06F 16/27 (2019.01); G06Q 10/105 (2013.01); G06Q 30/0185 (2013.01); H04L 9/085 (2013.01); H04L 9/30 (2013.01); H04L 9/3213 (2013.01); H04L 2101/37 (2022.05)] | 17 Claims |
|
1. A system for key recovery, comprising:
an interface configured to:
receive a request to recover a user private key; and
a processor configured to:
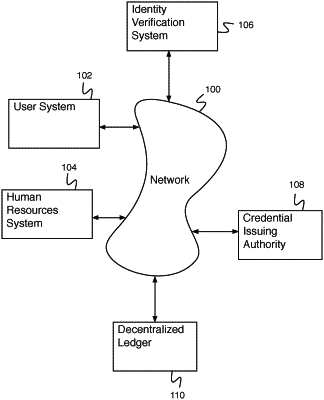
provide a request to a credential issuing authority for a first recovery key share, wherein the request includes a first identification validation credential, and wherein the first recovery key share is encrypted using a credential issuing authority public key associated with the credential issuing authority and is provided to the credential issuing authority;
query the credential issuing authority for a determination of a trusted organization using the first identification validation credential;
receive the first recovery key share and an encrypted key request token from the credential issuing authority;
provide a request to the trusted organization for a second recovery key share, wherein the request includes a second identification validation credential, and wherein the second recovery key share is encrypted using a trusted organization public key associated with the trusted organization and is provided to the trusted organization;
receive the second recovery key share from the trusted organization;
combine the first recovery key share and the second recovery key share to determine a recovered encryption key;
provide to the credential issuing authority the encrypted key request token and a request for an encrypted backup copy of the user private key;
receive the encrypted backup copy of the user private key from the credential issuing authority; and
determine the user private key using the recovered encryption key and the encrypted backup copy of the user private key.
|