| CPC H04L 63/20 (2013.01) [H04L 41/0894 (2022.05)] | 20 Claims |
|
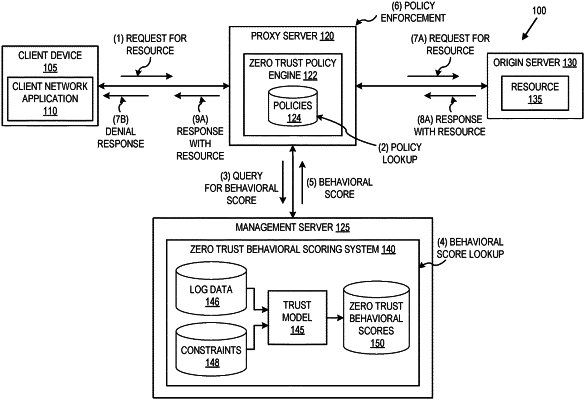
1. A computer-implemented method comprising:
retrieving access logs associated with a plurality of identities;
generating, using a trust model and based on the retrieved access logs, a plurality of behavioral scores for the plurality of identities respectively, wherein each behavioral score is dynamic, and wherein a value of a particular behavioral score for a particular identity increases in response to an access approval for that particular identity as indicated in the retrieved access logs and decreases in response to an access denial for that particular identity as indicated in the retrieved access logs;
receiving a first request to access a resource, the first request associated with a first identity of the plurality of identities;
determining that a zero trust access policy is applicable for the resource;
determining a first behavioral score for the first identity associated with the first request;
determining that the first behavioral score associated with the first identity satisfies a behavioral score threshold for the zero trust access policy;
providing the resource in response to the first request responsive to the determining that the first behavioral score associated with the first identity satisfies the behavioral score threshold for the zero trust access policy;
receiving a second request to access the resource, the second request associated with a second identity of the plurality of identities;
determining that the zero trust access policy is applicable for the resource;
determining a second behavioral score for the second identity associated with the second request;
determining that the second behavioral score associated with the second identity fails to satisfy the behavioral score threshold for the zero trust access policy; and
performing an action defined in the zero trust access policy responsive to the determining that the second behavioral score associated with the second identity fails to satisfy the behavioral score threshold for the zero trust access policy.
|