| CPC H04L 63/20 (2013.01) [G06F 9/45558 (2013.01); H04L 63/0209 (2013.01); G06F 2009/45591 (2013.01); G06F 2009/45595 (2013.01)] | 20 Claims |
|
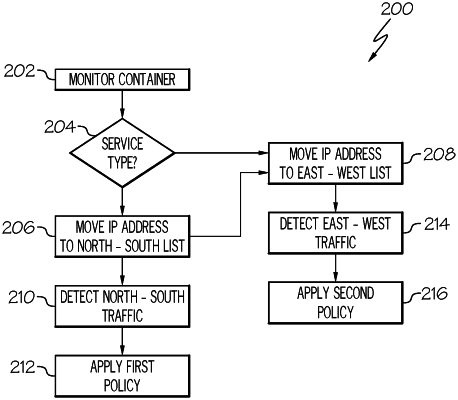
1. A method for processing computer network traffic, comprising:
monitoring, by one or more processors of a computer system, a computing environment including a plurality of containers, wherein the plurality of containers is instantiated within a container-based architecture;
determining, for at least one container of the plurality of containers, a service type and an IP address;
assigning, by the one or more processors of the computer system, the IP address of the at least one container of the plurality of containers having the determined service type to a first list of IP addresses;
assigning, by the one or more processors of the computer system, an IP address of each of the plurality of containers to a second list of IP addresses;
applying, by the one or more processors of the computer system, a first security policy for a first source of network traffic between the at least one container and a device external to the container-based architecture for processing by the at least one container having the determined service type and the IP address assigned to the first list of IP addresses;
managing a first traffic flow of the first source of network traffic between the at least one container and the device external to the container-based architecture according to the first security policy, wherein managing the first traffic flow includes generating an alert or preventing the first traffic flow by an intrusion prevention system (IPS) from entering the container-based architecture;
applying, by the one or more processors of the computer system, a second security policy for a second source of network traffic between the plurality of containers within the container-based architecture for processing by the containers having the IP addresses assigned to the second list of IP addresses; and
managing a second traffic flow of the second source of network traffic between the plurality of containers according to the second security policy, wherein managing the first traffic flow includes generating an alert or preventing, by the IPS, the second traffic flow from being exchanged between the plurality of containers within the monitored container-based architecture.
|