| CPC H04L 63/20 (2013.01) [G06F 12/10 (2013.01); H04L 9/0869 (2013.01); H04L 9/0894 (2013.01); H04L 9/3278 (2013.01); H04L 63/0245 (2013.01); H04L 63/10 (2013.01); G06F 2212/1024 (2013.01); G06F 2212/7201 (2013.01)] | 27 Claims |
|
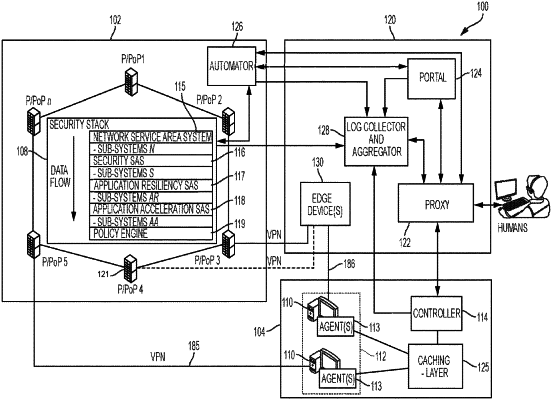
1. A system for protecting an enterprise network that is remote from the system, the system comprising:
one or more processors;
a non-transient computer readable medium having stored therein instructions executable by the one or more processors to:
control at least one of: (a) communications to and from the enterprise network according to a set of security policies, and (b) endpoint to endpoint connections within the enterprise network according to the set of security policies, wherein controlling endpoint to endpoint connections comprises receiving connection escalation requests from endpoint agents and replying to the connection escalation requests with responses that comprise actions for handling connections that are based on the set of policies, the endpoint agents running on endpoint devices;
receive a request for modifications to one or more policies of the set of security policies;
automatically generate a policy digest formatted according to a predefined format, the policy digest comprising the modifications;
generate, based upon the policy digest, one or more calls to one or more components within the enterprise network that control at least one of: (a) the communications to and from the enterprise network, and (b) the endpoint to endpoint connections within the enterprise network;
modify control, based on the one or more calls, of at least one of: (a) the communications to and from the enterprise network, and (b) the endpoint to endpoint connections within the enterprise network; and
wherein the communications for the enterprise network are routed through one or more perimeter points of presence and the one or more calls are one or more calls for modification of a security stack implemented by the one or more perimeter points of presence.
|