| CPC H04L 63/1483 (2013.01) [H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A method comprising:
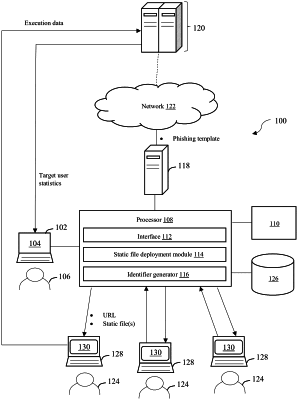
deploying at least one static file on a computing resource of a company network, wherein the computing resource is controlled by an operator of the company, and the at least one static file comprises code executable by web browsers and being accessible by a URL;
transmitting the URL that provides access to the at least static file to a target user device of a target user;
receiving a request for the URL that provides the access to the at least one static file from the target user device;
transmitting the at least one static file from the computing resource of the company network to the target user device, wherein the transmission causes execution of the code in a web browser of the target user device, the execution including:
obtaining a phishing script for the target user based on an identifier of the target user;
tracking user interactions with the URL via the web browser and according to the phishing script; and
sending, to a training server controlled by a third party phishing application provider, the user interactions as individual events, wherein each event indicates an event identifier and the identifier of the target user.
|