| CPC H04L 63/1433 (2013.01) [H04L 63/1425 (2013.01)] | 20 Claims |
|
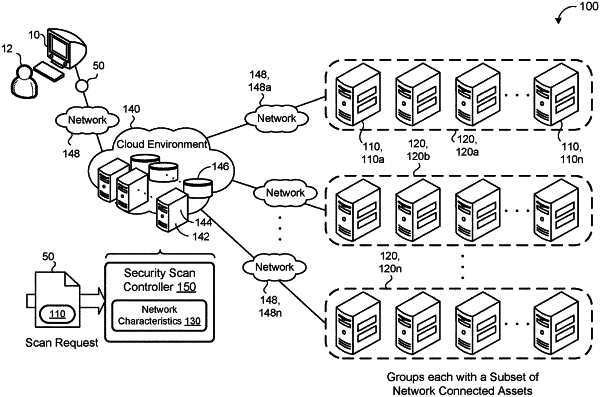
1. A computer-implemented method when executed by data processing hardware causes the data processing hardware to perform operations comprising:
receiving a scan request requesting to scan a set of network-connected assets, each network-connected asset in the set of network-connected assets designated for a network scan and associated with corresponding network characteristics;
partitioning the set of network-connected assets into a plurality of groups based on the corresponding network characteristics associated with each network-connected asset, each group comprising a different respective subset of network-connected assets of the set of network-connected assets; and
for each respective group of the plurality of groups, simultaneously:
determining an ordered list for scanning each network-connected asset in the respective subset of network-connected assets partitioned into the respective group;
scanning a first network-connected asset of the respective group based on the ordered list;
after scanning the first network-connected asset, determining a post-scan health status of the first network-connected asset;
determining, using the post-scan health status, that a health of the first network-connected asset is degraded; and
in response to determining that the health of the first network-connected asset is degraded, halting scanning of further network-connected assets in the respective group.
|