| CPC H04L 63/1425 (2013.01) [H04L 63/029 (2013.01); H04L 63/0236 (2013.01); H04L 63/1416 (2013.01); H04L 63/20 (2013.01)] | 21 Claims |
|
1. A method, comprising:
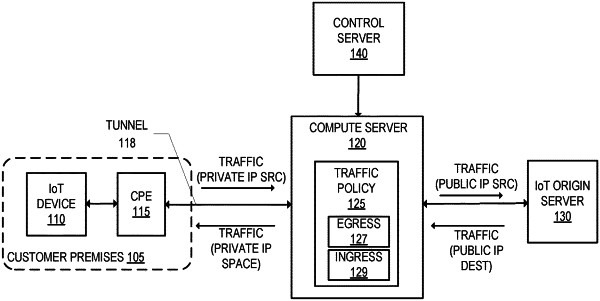
receiving at a compute server of a distributed cloud computing network, over a tunnel established between a customer-premises equipment (CPE) and the compute server, first traffic from an Internet-of-Things (IoT) device that is connected to the CPE, wherein the first traffic is destined to a first destination;
enforcing an egress traffic policy to determine whether the first traffic is permitted to be transmitted to the first destination, wherein the egress traffic policy specifies that traffic is only allowed to be transmitted to a destination associated with a service of the IoT device, wherein the destination associated with the service of the IoT device is external to the distributed cloud computing network;
determining, based on the enforcing of the egress traffic policy, that the first traffic is permitted to be transmitted to the first destination because the first destination corresponds to the destination associated with the service of the IoT device, and responsive to this determination, transmitting the first traffic to the first destination;
receiving, at the compute server, second traffic that is destined to the IoT device;
enforcing an ingress traffic policy to determine whether the second traffic is permitted to be transmitted to the IoT device;
determining, based on the enforcing of the ingress traffic policy, that the second traffic is not permitted to be transmitted to the IoT device, and responsive to this determination, dropping the second traffic;
receiving at the compute server over the tunnel, third traffic from the IoT device that is connected to the CPE, wherein the third traffic is destined to a second destination;
enforcing the egress traffic policy to determine whether the third traffic is permitted to be transmitted to the second destination; and
determining, based on the enforcing of the egress traffic policy, that the third traffic is not permitted to be transmitted to the second destination because the second destination does not correspond to the destination associated with the service of the IoT device, and responsive to this determination, dropping the third traffic.
|