| CPC H04L 63/1425 (2013.01) [H04L 63/1441 (2013.01); H04L 2463/121 (2013.01)] | 20 Claims |
|
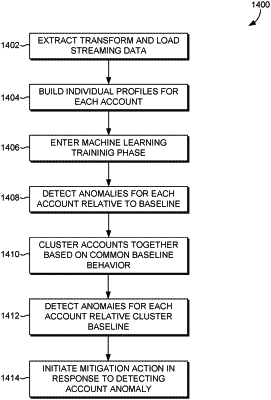
1. A computer-implemented method, comprising:
organizing, based on a first time series, a first set of raw machine data generated by a first client device to generate a first behavior profile for a first account of a plurality of accounts operating on the first client device, wherein separate time series are stored for each account, wherein the separate time series are organized according to a relationship the plurality of accounts have with each other, wherein:
the first time series comprises a first set of entries, and
at least one of the first set of entries includes (i) a first scripting language command, and (ii) a corresponding time associated with the first scripting language command;
generating, based on the first behavior profile, a baseline behavior associated with the first account;
comparing the baseline behavior to a second account associated with a second set of raw machine data received from the first client device, wherein the second set of raw machine data is associated with subsequent network traffic received by or transmitted from the first client device;
detecting an anomaly in the second set of raw machine data when a difference between the baseline behavior and the second account exceeds a threshold; and
initiating a mitigation action with respect to the first client device in response to detecting the anomaly.
|