| CPC H04L 63/1416 (2013.01) [B60R 16/023 (2013.01); H04L 67/12 (2013.01)] | 7 Claims |
|
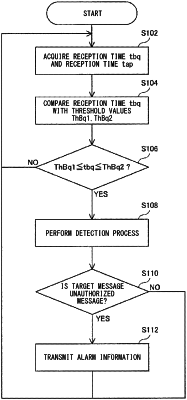
5. A detection method performed in a detection device configured to detect an unauthorized message in an in-vehicle network, the method comprising:
monitoring, as target messages, an authorized message being periodically transmitted and the unauthorized message in the in-vehicle network, and monitoring a reference message being periodically transmitted;
based on a monitoring result, calculating a time difference between a time corresponding to a transmission time of the target message and a time corresponding to a transmission time of the reference message; and
based on the calculated time difference, performing a detection process of detecting the unauthorized message, wherein
the authorized message and the reference message have different transmission cycles,
as the detection process, the performing includes determining whether or not the target message is an unauthorized message, according to a criterion,
performing the detection process while switching a plurality of criteria, and
a number of criteria to be used in the detection process is determined based on a least common multiple between the transmission cycle of the authorized message and the transmission cycle of the reference message, and on the transmission cycle of the authorized message.
|