| CPC G06Q 20/4014 (2013.01) [G06Q 20/308 (2020.05); G06Q 20/4015 (2020.05); H04W 4/023 (2013.01); H04W 12/06 (2013.01); H04W 12/63 (2021.01)] | 19 Claims |
|
1. An apparatus, comprising:
a processing circuit; and
logic stored in computer memory and executed on the processing circuit, the logic operative to cause the processing circuit to:
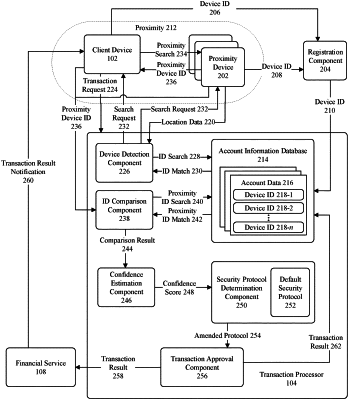
process registration information comprising at least one identifier for each computing device of a plurality of computing devices having authority over a financial account, and wherein a first computing device of the plurality of computing devices comprising an integrated circuit being configured to execute electronic transactions against the financial account;
receive, from the first computing device, a transaction request to perform a transaction utilizing the financial account;
determine the first computing device is a member of the plurality of computing devices based upon the registration information;
determine a first authentication protocol to use to authenticate the transaction request based on receipt of, via the first computing device, data from a second computing device, wherein the first computing device and the second computing device are within a defined distance and the data identifies the second computing device, wherein the second computing device is another member of the plurality of computing devices based upon the registration information and the data identifying the second computing device, the first authentication protocol forgoes performance of at least one authentication factor of a multifactor authentication process; and
determine a second authentication protocol to use to authenticate the transaction request based on the first device not providing the data from the second device, the second authentication protocol comprises performance of the multifactor authentication process.
|