| CPC G06F 21/6218 (2013.01) [G06F 21/445 (2013.01); G06F 21/554 (2013.01); G06F 21/568 (2013.01); G06F 2221/2101 (2013.01)] | 18 Claims |
|
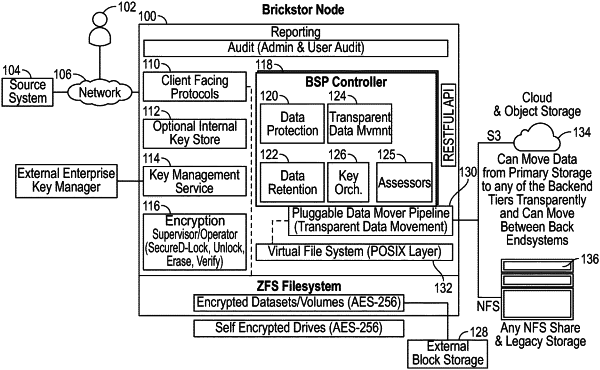
1. A system comprising:
a file system; and
an architecture installed on the file system, the architecture being configured to protect the file system in a zero-trust manner from a malicious attack by a source system, the architecture comprising a controller that is configured to:
determine file-level operations of files in the file system that are indicative of a malicious event;
block a user account or machine address interacting with the files over a network;
prevent data exfiltration or data corruption of the files;
provide an alert to an administrator regarding the files;
place snapshot holds on immutable snapshots so files that have been modified or deleted can be recovered to prior versions and snapshots are available;
identify the files that were associated with the malicious event;
present a graphical user interface that allows for restoration of the files from an immutable backup copy of the file system; and
restore the files as requested.
|