| CPC G06F 21/577 (2013.01) [G06F 21/566 (2013.01); G06N 20/00 (2019.01); G06F 2221/033 (2013.01); G06F 2221/034 (2013.01)] | 14 Claims |
|
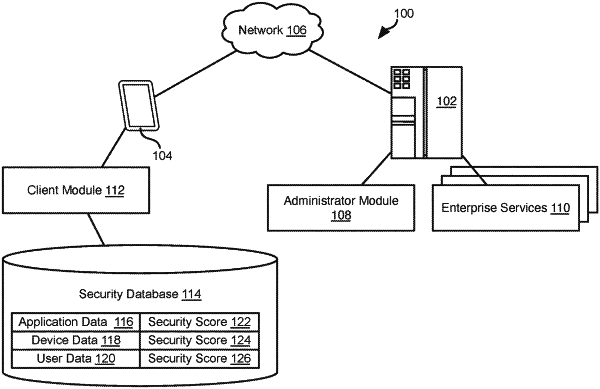
1. A method for characterizing security comprising:
receiving, by a computing device, a plurality of factors describing applications installed on a mobile device;
assigning, by the computing device, an application score to the plurality of factors; and
calculating a security score for the mobile device based on the application score;
wherein the plurality of factors includes one or more of:
a number of malware on the mobile device;
a level or risk associated with malware on the mobile device;
a number of the applications that are side-loaded applications not obtained from a trusted source;
a number of the applications accessing cloud storage;
a number of the applications that are messaging applications;
a number of the applications that are out of date; or
a number of the applications that are no longer available in an application store
receiving, by the computing device, authentication behavior of a user with respect to a mobile device for a time period;
processing, by the computing device, the authentication behavior to obtain an authentication score; and
combining the authentication score with the application score to obtain the security score for the mobile device;
wherein the authentication behavior includes one or more of number of failed attempts, login times, login locations, or networks used.
|