| CPC G06F 21/57 (2013.01) [G06F 21/32 (2013.01); H04L 9/0816 (2013.01); H04L 9/3226 (2013.01)] | 20 Claims |
|
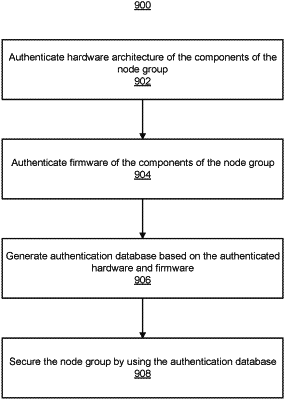
1. A method for securing a plurality of compute nodes, comprising:
authenticating a hardware architecture of each of a plurality of components of the compute nodes;
authenticating a firmware of each of the plurality of components; and
generating an authentication database comprising a plurality of authentication descriptions that are based on the authenticated hardware architecture and the authenticated firmware, wherein a policy for securing a specified subset of the plurality of compute nodes is implemented by using the authentication database.
|