| CPC G06F 21/564 (2013.01) [G06F 18/23 (2023.01); G06F 21/552 (2013.01)] | 20 Claims |
|
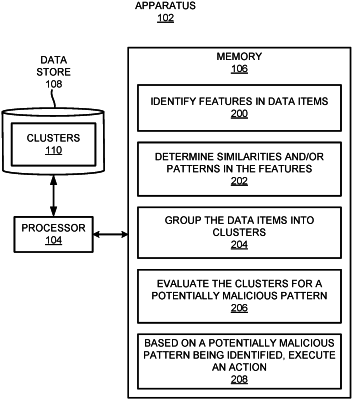
1. An apparatus comprising:
a processor; and
a memory on which is stored machine-readable instructions that when executed by the processor, cause the processor to:
identify features in a plurality of messages communicated between senders and receivers, wherein the identified features include information related to the senders of the plurality of messages;
determine common patterns in the identified features in the plurality of messages, including identifying messages that were received from a same sender within a predefined time window;
group the plurality of messages into a plurality of clusters based on the common patterns in the identified features in the plurality of messages;
evaluate the plurality of clusters separately from one another to identify a potentially malicious pattern among the messages in one or more of the plurality of clusters, wherein a potentially malicious pattern is identified in a particular cluster when, in the particular cluster, a count of the messages that were received from the same sender within the predefined time window exceeds a threshold number; and
based on the potentially malicious pattern being identified in the particular cluster, execute an action with regard to the messages in the particular cluster, wherein the action comprises one of notification or removal of specific messages from the particular cluster.
|