| CPC H04W 12/06 (2013.01) | 6 Claims |
|
1. A process for authentication and authorization of an Intended User to access a hard asset controlled by a point of interaction (“POI”), wherein the POI is comprised of electronic hardware, a POI program stored in a POI digital medium and means to control a physical switch which allows access to the hard asset, comprising the steps of:
initiating an interaction between the POI and a mobile digital device provisioned with a program stored in a first digital medium configured for use with the POI;
sending, from the POI to the mobile digital device, a response which is comprised of a first realm identifier, a POI identifier and a request for a credential needed to access the hard asset;
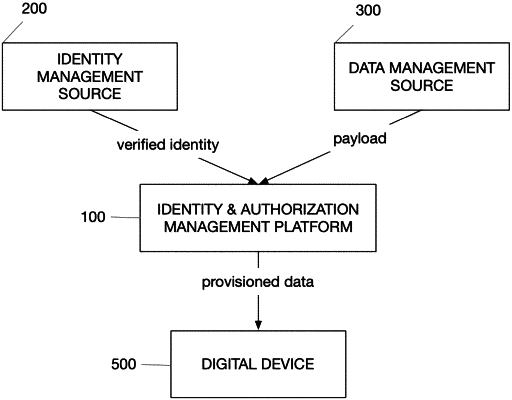
receiving, at the POI from the mobile digital device, an access transaction request which is comprised of a transaction cryptogram from which the credential can be authenticated, wherein the credential is comprised of a first set of elements signed by a private key of the mobile digital device previously generated for a first realm, including at least a first element sent by the POI to the mobile digital device in the response and a second element sent by an Identity and Authorization Management Platform (“IDAMP”), operated by at least one hardware processor, to the mobile digital device in a payload; a second set of elements signed by a private key of the IDAMP; and an IDAMP payload signature;
at the POI, either initiating a service request for processing over a network connection or initiating an offline authentication to determine whether or not the physical switch should be activated to allow the Intended User access to the hard asset, wherein
if a service request for processing is initiated over the network connection, the service request is sent over the network connection to the Identity and Authorization Management Platform to validate whether the Intender User is authorized to access the hard asset by the mobile digital device; and
receiving, at the point of interaction from the network Identity and Authorization Management Platform, an authorization response; or
if an offline data authentication is initiated, and the POI has an offline capability via an offline Identity and Authorization Management Platform, validating whether the Intender User is authorized to access the hard asset by the mobile digital device;
wherein validating whether the Intender User is authorized to access the hard asset by the mobile digital device will only result in authorizing access to the hard asset when all of the following are true:
(1) it is verified that the mobile digital device used the private key of the mobile digital device previously generated for the realm to generate a mobile digital device payload signature contained in the first set of elements;
(2) it is verified that the second set of elements has not been altered; and
(3) the Payload contains a second realm identifier which matches the first real identifier.
|