| CPC H04L 9/3213 (2013.01) [H04L 9/0819 (2013.01); H04L 9/0838 (2013.01)] | 20 Claims |
|
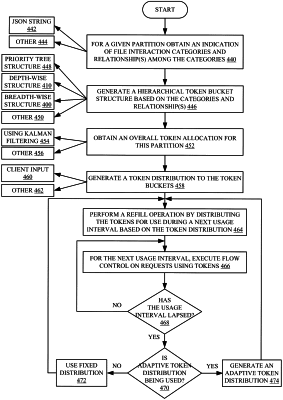
1. A computer implemented method, comprising:
receiving, at a token issuer component, a token request that corresponds to a token requestor and requests a token representing permission to record a file interaction in an index;
identifying a particular category of file interaction for which the token is requested;
accessing a portion of a token bucket structure of token buckets based on the particular category of file interactions, the token bucket structure including:
a first token bucket corresponding to a first type of file interaction belonging to a first category of file interactions, the first token bucket having a first number of available tokens, and
a second token bucket corresponding to a second type of file interaction belonging to a second category of file interactions, the second type of file interaction being different than the first type of file interaction, and the second token bucket having a second number of available tokens; and
based on determining that there are enough available tokens, in one of the first token bucket or the second token bucket corresponding to the particular category of file interactions, to service the token request,
providing the token to the token requestor.
|