| CPC H04L 9/0891 (2013.01) [H04L 9/003 (2013.01); H04L 9/16 (2013.01)] | 18 Claims |
|
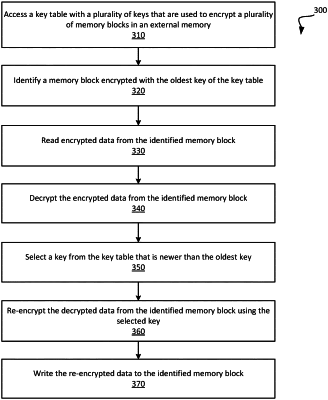
1. A computer-hardware implemented method comprising:
accessing a key data structure comprising a plurality of encryption keys that are used to encrypt a plurality of memory blocks in an external memory;
identifying a memory block of the plurality of memory blocks that is encrypted with an oldest encryption key in the key data structure;
reading encrypted data from the identified memory block;
decrypting the encrypted data from the identified memory block;
selecting an encryption key from the key data structure, wherein the selected encryption key is newer than the oldest encryption key;
re-encrypting the decrypted data from the identified memory block using the selected encryption key;
allowing an inline encryption engine to take precedence over updates from a memory update encryption engine that operates in tandem with the inline encryption engine; and
writing the re-encrypted data to the identified memory block.
|