| CPC H04L 9/0825 (2013.01) [H04L 9/088 (2013.01); H04L 9/0838 (2013.01); H04L 9/3247 (2013.01); H04L 9/3271 (2013.01); H04L 67/306 (2013.01)] | 16 Claims |
|
1. A method comprising:
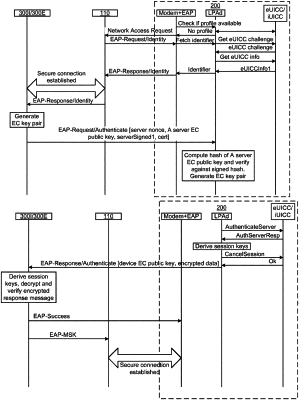
a communication device transmitting to a network node a network attachment request in response to determining that the communication device does not have a remote subscription profile, wherein the network node is remote from the communication device and wherein the network node is not a component of the communication device;
after transmitting the network attachment request, the communication device receiving a request message transmitted by the network node;
in response to receiving the request message transmitted by the network node, the communication device transmitting a primary message to the network node, wherein the primary message comprises an identity module challenge obtained from an identity module comprising an integrated circuit card (ICC) within the communication device after receiving the request message transmitted by the network node, and wherein the network node is configured to forward the identity module challenge to an authentication server in response to identifying the authentication server using a network address of the authentication server included in the primary message;
the communication device receiving, from the network node, a second message that was transmitted by the authentication server, wherein the second message comprises an ephemeral public key of the authentication server, an authentication server challenge, and an authentication server signature, wherein the authentication server signature is based on the ephemeral public key of the authentication server, the authentication server challenge, and the identity module challenge and follows a format used for handling the remote subscription profile download to the identity module;
the communication device transmitting a third message towards the authentication server in response to receiving the second message, wherein the third message comprises an ephemeral public key of the communication device and an identity module signature, wherein the identity module signature is based on identity module credentials used for the remote subscription profile download to the identity module and is based on the ephemeral public key of the communication device and the authentication server challenge and follows the format used for the remote subscription profile download to the identity module;
the communication device establishing a secret using the ephemeral public key of the authentication server and a private key corresponding to the ephemeral public key of the communication device;
the communication device generating a master session key (MSK) using the established secret;
the communication device obtaining data for transmission to the network node;
the communication device using the MSK to encrypt the data, thereby producing encrypted data;
and the communication device transmitting the encrypted data to the network node.
|