| CPC H04L 9/0643 (2013.01) [G06F 18/22 (2023.01); H04L 63/205 (2013.01)] | 20 Claims |
|
1. A method performed by at least one computer processor executing computer program instructions stored on at least one non-transitory computer-readable medium, the method comprising:
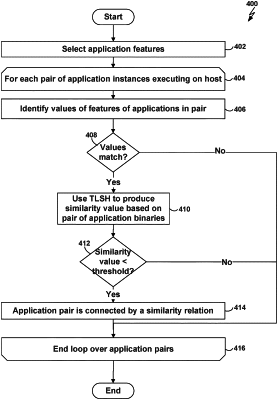
identifying, on a plurality of systems, one or more applications that have a similarity relation to a reference application;
determining network security policies for the one or more applications, wherein the network security policies are determined for the reference application and wherein the one or more applications are previously unseen applications that are given the network security policies for the reference application based on the similarity relation;
determining a subset of the network security policies that is relevant to one of the plurality of systems, wherein the subset of network security policies is determined based on the one or more applications on the system, if that application or an application that has a similarity relation to that application is installed and/or executing on the system; and
applying the subset of network security policies to communications between the plurality of systems.
|