| CPC H04L 63/1433 (2013.01) [G06N 5/01 (2023.01); H04L 2012/40286 (2013.01)] | 10 Claims |
|
1. An automated method for conducting a cyber risk assessment of a Cyber Physical System (CPS), comprising the steps of:
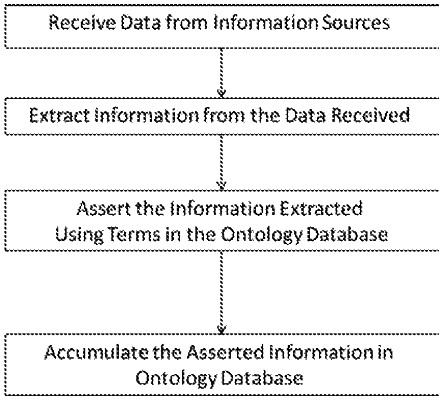
extracting and encoding information from a plurality of knowledge domains using a CPS Information Extraction System;
modeling relationships across the plurality of domains using a CPS Semantic Model;
storing the information in a Cyber-Risk Information Database in accordance with a plurality of ontologies provided by the CPS Semantic Model;
plotting an attack graph using an Attack Graph Algorithm employing an electrical circuit analogy;
evaluating a chain of cyber threat impacts using a Chain of Impacts Algorithm;
evaluating the criticality of any of a system, a subsystem, or a component, using a CPS Criticality Algorithm;
evaluating the cyber risk at the component and system levels in a CPS using a Threat Assessment Heuristic (THRASH) Cyber Risk Algorithm; and
outputting the cyber risk assessment.
|