| CPC H04L 63/0853 (2013.01) [H04L 63/0263 (2013.01); H04L 63/0876 (2013.01); H04L 67/52 (2022.05); G06Q 30/018 (2013.01); H04L 2463/082 (2013.01)] | 20 Claims |
|
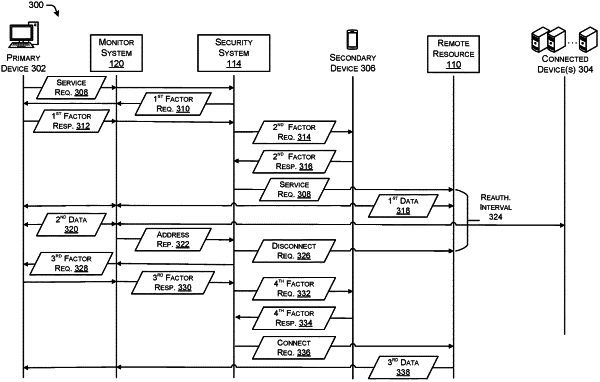
15. A security system, comprising:
at least one processor; and
one or more non-transitory media storing instructions that, when executed by the system, cause the security system to perform operations comprising:
performing, at a first time, a first authentication of a primary device connecting to a resource by:
transmitting, to the primary device, a request for a first authentication factor;
receiving, from the primary device, the first authentication factor;
based on receiving the first authentication factor, transmitting, to the primary device or to a secondary device, a request for a second authentication factor;
receiving, from the primary device or the secondary device, the second authentication factor; and
based on receiving the second authentication factor, connecting the primary device to the resource;
receiving, from a monitoring system, a message indicating internet protocol (IP) addresses of endpoint devices exchanging data with the primary device;
determining first physical locations of the endpoint devices based on the IP addresses;
determining that at least one of the first physical locations of the endpoint devices is anomalous with respect to second physical locations of other devices that were previously exchanging data with the primary device;
based on determining that at least one of the first physical locations of the endpoint devices is anomalous with respect to the second physical locations of other devices that were previously exchanging data with the primary device:
determining a reauthentication interval; and
selecting a third authentication factor; and
at a second time that is after the first time by the reauthentication interval:
disconnecting the primary device from the resource; and
based on disconnecting the primary device from the resource, triggering a second authentication of the primary device by transmitting, to the primary device or to the secondary device, a request for the third authentication factor.
|