| CPC G06Q 20/40155 (2020.05) [G06Q 20/3224 (2013.01); G06Q 20/4014 (2013.01); G06Q 20/4093 (2013.01)] | 18 Claims |
|
1. A method comprising:
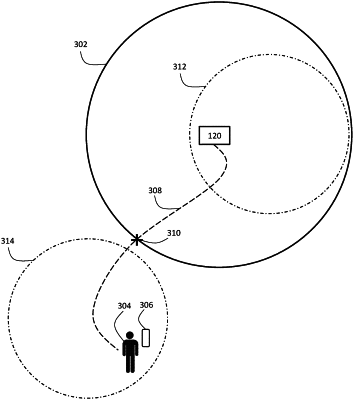
identifying, by one or more processors, a first trigger event based on a financial device profile, wherein the first trigger event indicates a first proximal distance threshold is exceeded for a first device associated with a user relative to a second device associated with the user, and wherein the first device is capable of executing financial transactions;
querying, by the one or more processors, the first device for a last known location where the first device did not exceed the first proximal distance relative to the second device;
identifying, by the one or more processors, a first network device at the last known location for the first device and a second network device at a location of the second device, wherein the first network device is positioned in a vicinity of the first device at the last known location and the second network device is position in a vicinity of the second device;
querying, by the one or more processors, the first network device in the vicinity of the first device and the second network device in the vicinity of the second device to confirm a first location for the first device and a second location for the second device;
responsive to receiving a first confirmation from the first network device of the first location for the first device and a second confirmation from the second network device of second location for the second device, validating, by the one or more processors, the first trigger event based on the first confirmation and the second confirmation;
applying, by the one or more processors, a first temporal lock on the first device preventing future executions of financial transactions based on the validating of the first trigger event; and
responsive to validating the user associated with the second device, updating, by the one or more processors, the financial device profile based at least on the first validation of the first trigger event and the first location for the first trigger event.
|