| CPC G06Q 20/3678 (2013.01) [H04L 9/0822 (2013.01); G06Q 2220/00 (2013.01)] | 18 Claims |
|
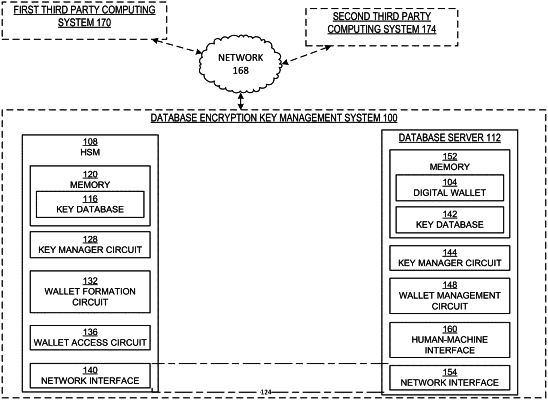
1. A method, comprising:
generating a cryptogram by encrypting, by a hardware security module (HSM), a keyed-hash message authentication code (HMAC) key by a master key encryption key (MK);
transmitting, by the HSM to a database server, the cryptogram;
destroying, by the HSM, the cryptogram at the HSM, in response to the transmitting the cryptogram to the database server;
receiving, by the HSM from the database server, the cryptogram and an identifier (ID) generated by the database server;
generating, by the HSM, a wallet password based on the ID and the received cryptogram;
generating, by the HSM, a digital wallet comprising a data encryption key (DK) retrievable only via the wallet password;
transmitting, by the HSM to the database server, the digital wallet comprising the DK without the wallet password;
destroying, by the HSM, the wallet password in response to the transmitting the DK to the database server;
decrypting, by the HSM, the received cryptogram into a decrypted HMAC key;
regenerating, by the HSM, the wallet password using the ID and the decrypted HMAC key;
encrypting, by the HSM, the regenerated wallet password; and
transmitting, by the HSM to the database server, the encrypted regenerated wallet password,
wherein the database server is configured to decrypt the encrypted regenerated wallet password, and retrieve the DK from the digital wallet using the decrypted regenerated wallet password.
|