| CPC G06F 21/577 (2013.01) [G06N 20/00 (2019.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
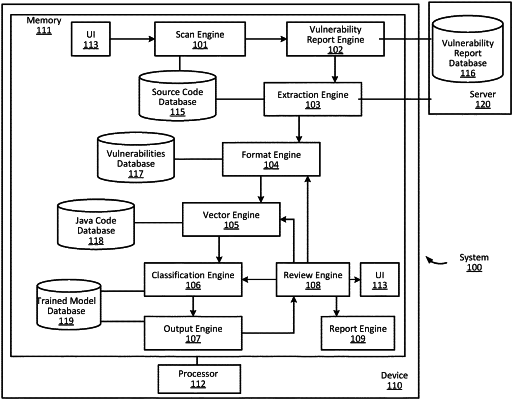
1. A system for assessing software vulnerability, comprising:
a memory to store executable instructions; and
a processor adapted to access the memory, the processor further adapted to execute the executable instructions stored in the memory to:
access an automated triage rule library comprising a plurality of pre-defined automated triage policies corresponding to a plurality of predetermined vulnerability types, wherein each automated triage policy comprises a decision tree for determining whether one of the plurality of predetermined vulnerability types is exploitable;
access a machine learning model library for probabilistic determination of whether one of the plurality of predetermined vulnerability types is exploitable;
obtain an electronic document listing potential vulnerability issues of a software product based on scanning source code of the software product;
determine whether the potential vulnerability issues are associated with one of the plurality of predetermined vulnerability types;
when it is determined that the potential vulnerability issues are associated with the one of the plurality of predetermined vulnerability types:
classify whether the software product is exploitable among classes of being exploitable, not exploitable, or suspicious of exploitability based on a rule-based deterministic classifier for processing the electronic document using an automated triage policy retrieved from the automated triage rule library associated with the one of the plurality of predetermined vulnerability types and based on a corresponding decision tree;
determine probabilistically whether the software product is exploitable based on a pretrained machine-learning probabilistic classifier; and
use an arbitrator to determine which classifier is more trustworthy when there is a classification conflict; and
otherwise, when it is determined that the potential vulnerability issues are not associated with the one of the plurality of predetermined vulnerability types, only determine probabilistically whether the software product is exploitable based on the pretrained machine-learning probabilistic classifier.
|